The Curse of Encryption - Breaking Through Encryption Barriers in Penetration Testing
Automated web penetration testing tools like BurpSuite Scanner, ZAP scanner, SQLMap, and Commix and fuzzing tools like ffuf, wfuzz, etc. are widely used in the cybersecurity community for their effectiveness in identifying vulnerabilities and securing web applications. These tools automate various aspects of the testing process, saving time and effort for pentesters.
However, these tools can face limitations when encountering security mechanisms such as encryption. Encryption is used to secure sensitive data in transit, ensuring that it cannot be intercepted and read by unauthorized parties. While encryption is crucial for protecting data, it can pose challenges for penetration testing tools that rely on injecting payloads into web applications to identify vulnerabilities.
In scenarios where encryption is implemented, the HTTP traffic is encrypted, making it difficult for traditional penetration testing tools to inject payloads and detect vulnerabilities. This limitation can hinder the effectiveness of these tools in identifying certain types of security vulnerabilities, particularly those that require the manipulation of HTTP requests and responses.
To address this challenge, The BrowserBruter was developed. BrowserBruter is a specialized tool designed to overcome the limitations posed by encryption and other security mechanisms. By utilizing browser automation techniques, BrowserBruter is able to interact with web applications at a higher level, bypassing the encryption and injecting payloads in a way that traditional tools cannot. This allows BrowserBruter to effectively identify vulnerabilities and security issues that may be missed by other tools.
For example, consider the following scenario:
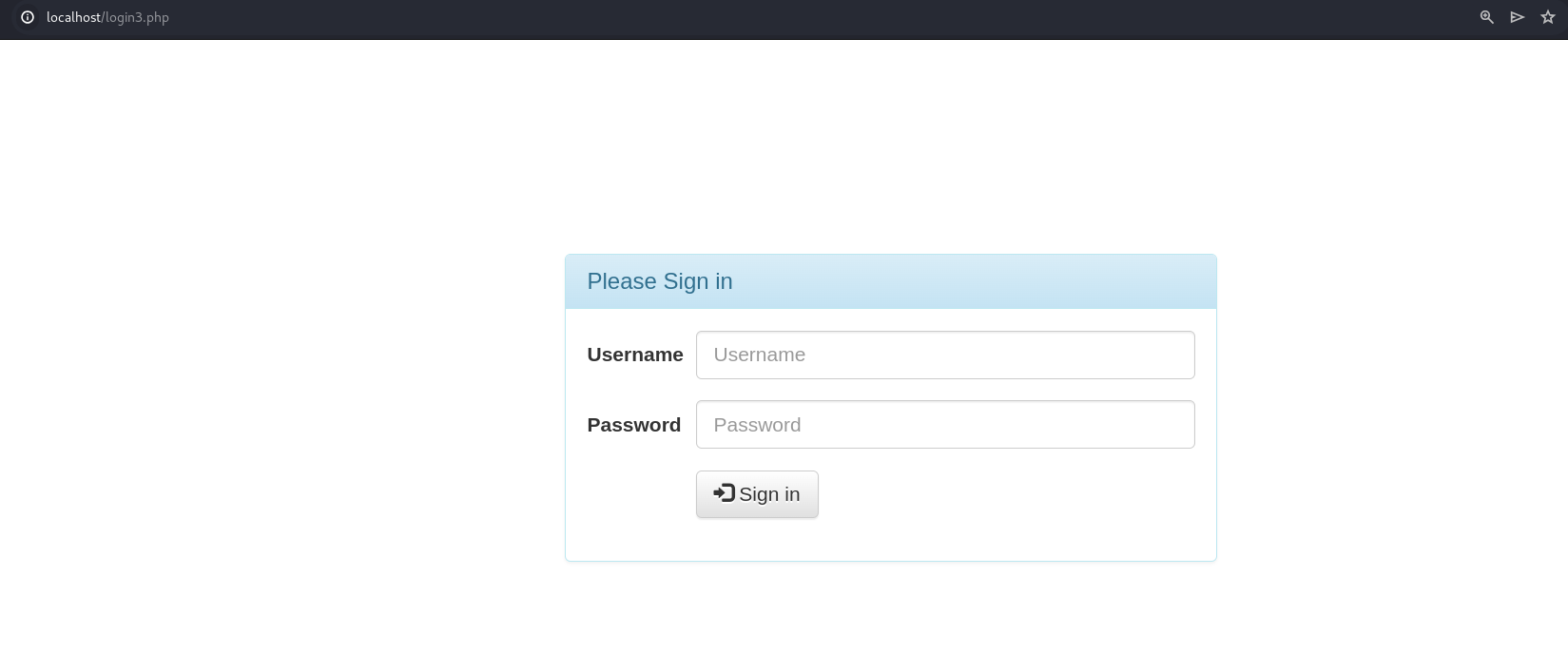
Here, we encounter a login page with username and password fields and a 'Sign in' button. Let's fill in these fields and press the 'Sign in' button.
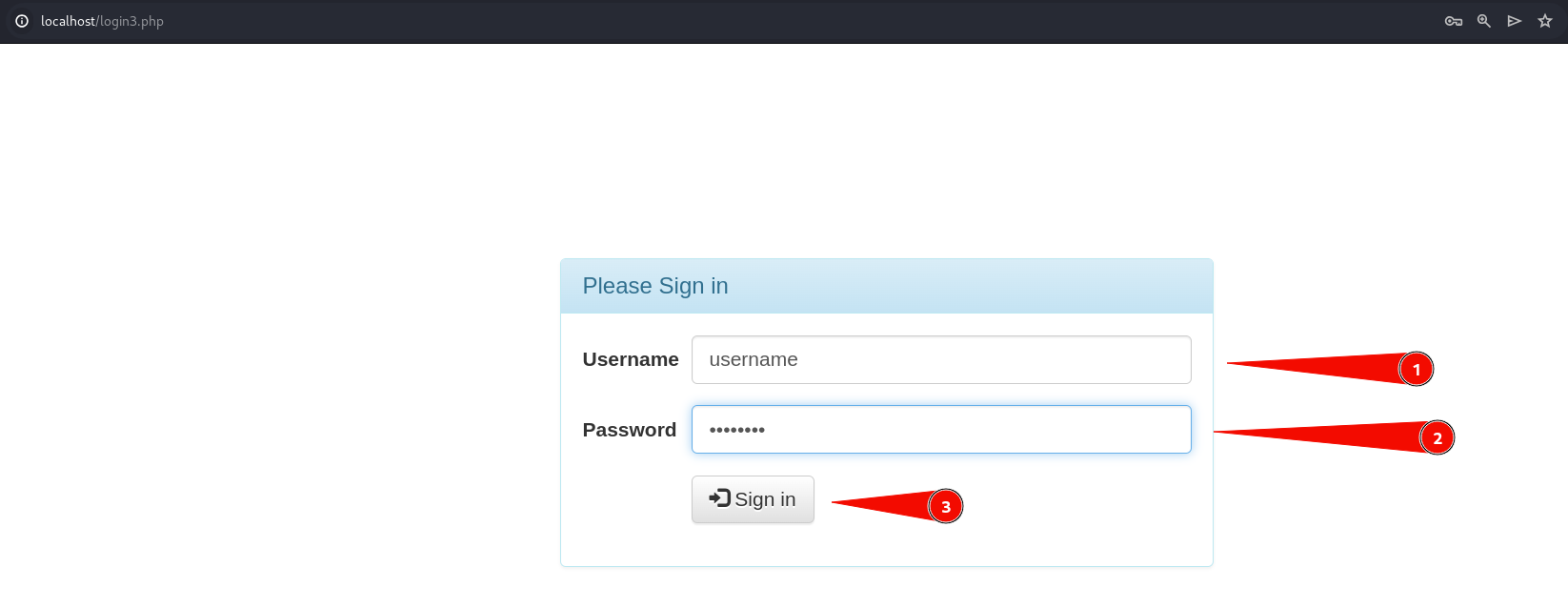
As expected, the server responds with a 'Username does not exist' message.
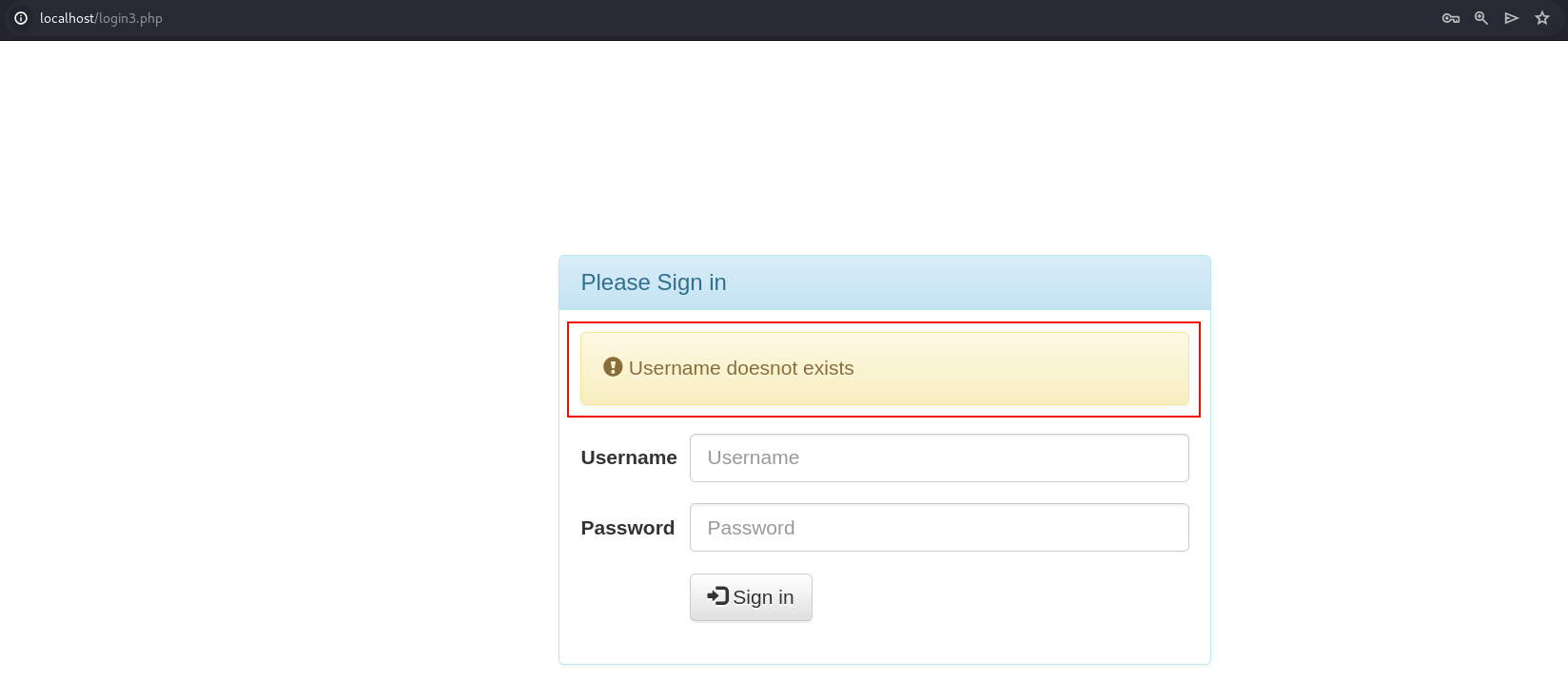
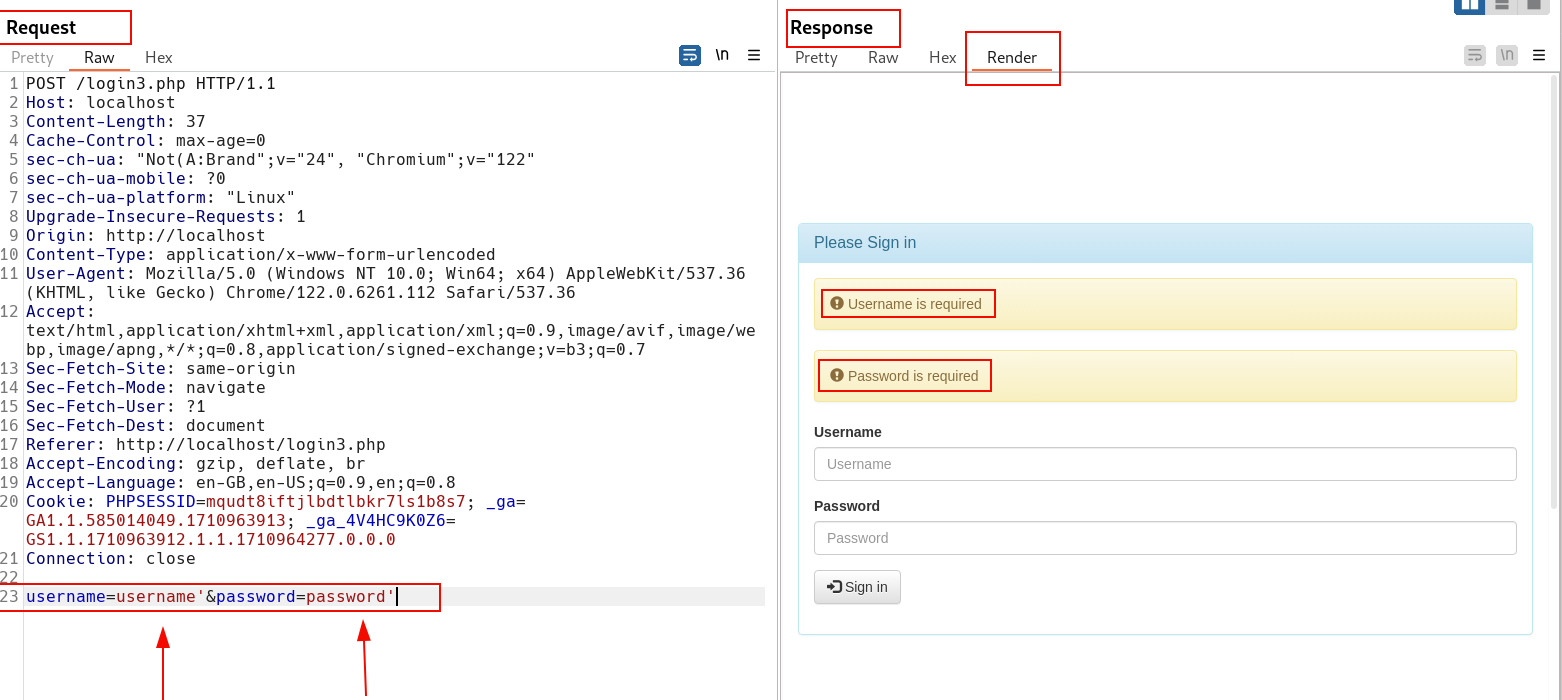
Let us intercept the HTTP request for this login page.
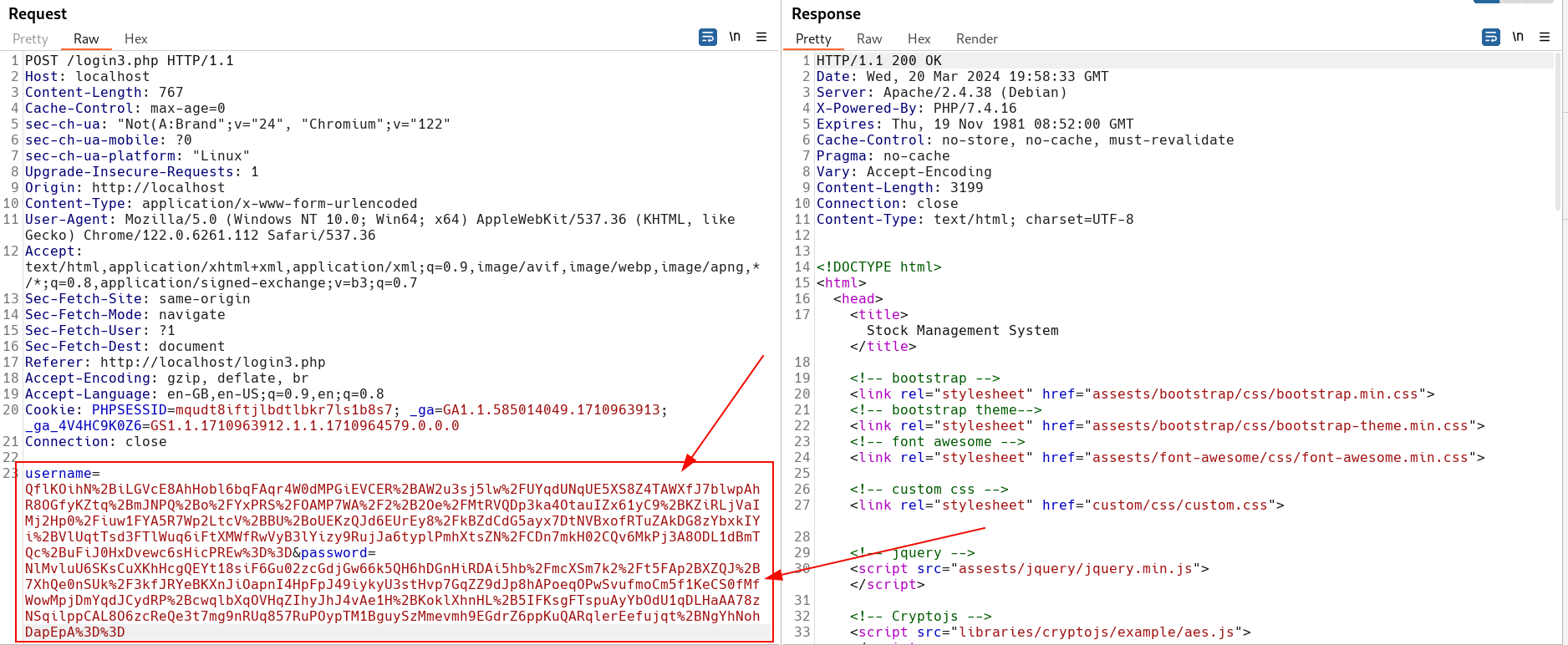
As shown above, the values inserted into the username and password fields are encrypted and appear as gibberish.
Now, if we try to inject malicious input and send it to the server, the server will respond as if the username and password parameters are empty, as it does not understand the format of the data we are sending.
Here's what's actually happening:
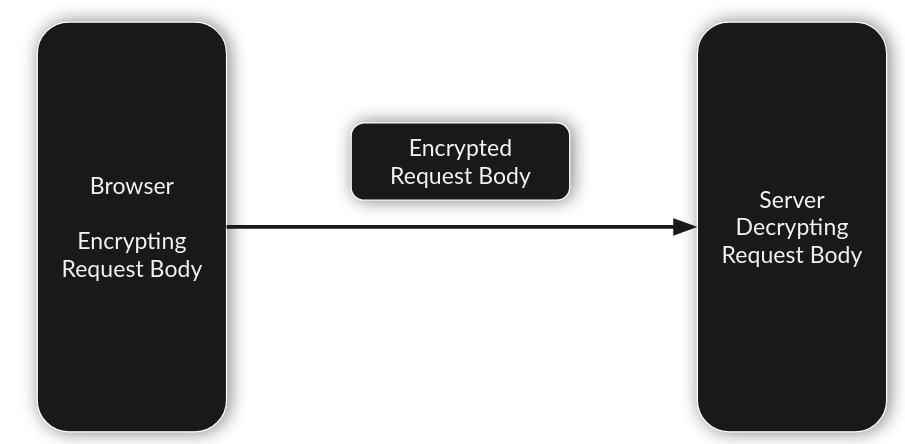
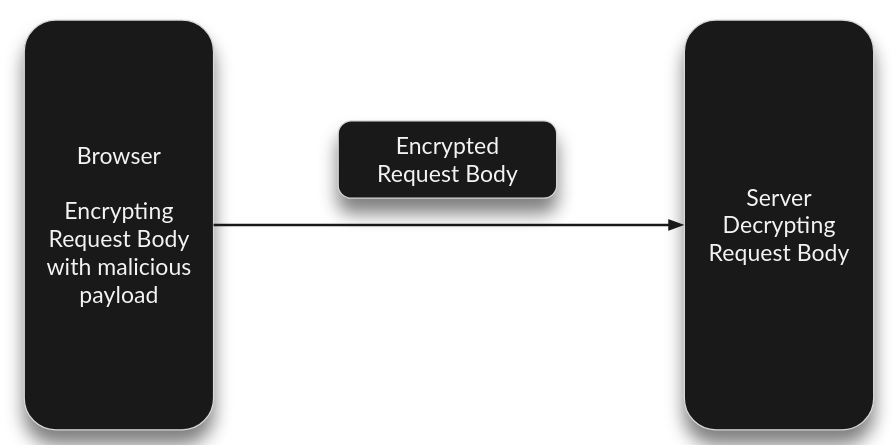
The browser is sending the inserted input in a predefined format, i.e., encrypted format. The server expects the data to be in a particular format.
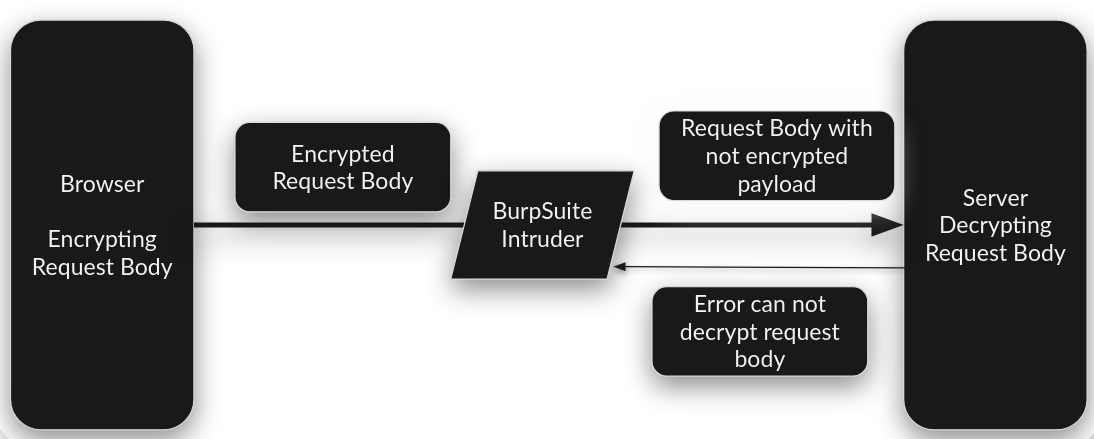
When we manipulate the HTTP request, we are altering the format of the data in which the server expects inputs to be. This causes the server to throw an error because it cannot parse this data as it is not in the expected format, i.e., encrypted format.
And here is a video clip demonstrating the same scenario:
Now, this particular login page is vulnerable to SQL Injection and Brute Force Attacks but We will never be able to found these vulnerabilities using any of the available tools.
Scanning for SQL Injection using SQLMap
In the video demonstration below, we attempt to identify a SQL Injection vulnerability in the username and password fields of our encrypted web application's login page.
As depicted, due to encryption, SQLMap is unable to detect the vulnerability.
Scanning for SQL Injection using BurpSuite
In the video demonstration below, we attempt to identify a SQL Injection vulnerability in the username and password fields of our encrypted web application's login page. This time let us use the BurpScanner which is only available in Professional Edition of BurpSuite.
As depicted, due to encryption, Even BurpScanner is unable to detect the vulnerability.
Brute Forcing Login page using ffuf
Let's see if we can brute force this login page. Here, we are brute forcing the login page using ffuf and checking if we get 302 HTTP Response even after providing and entering valid credentials.
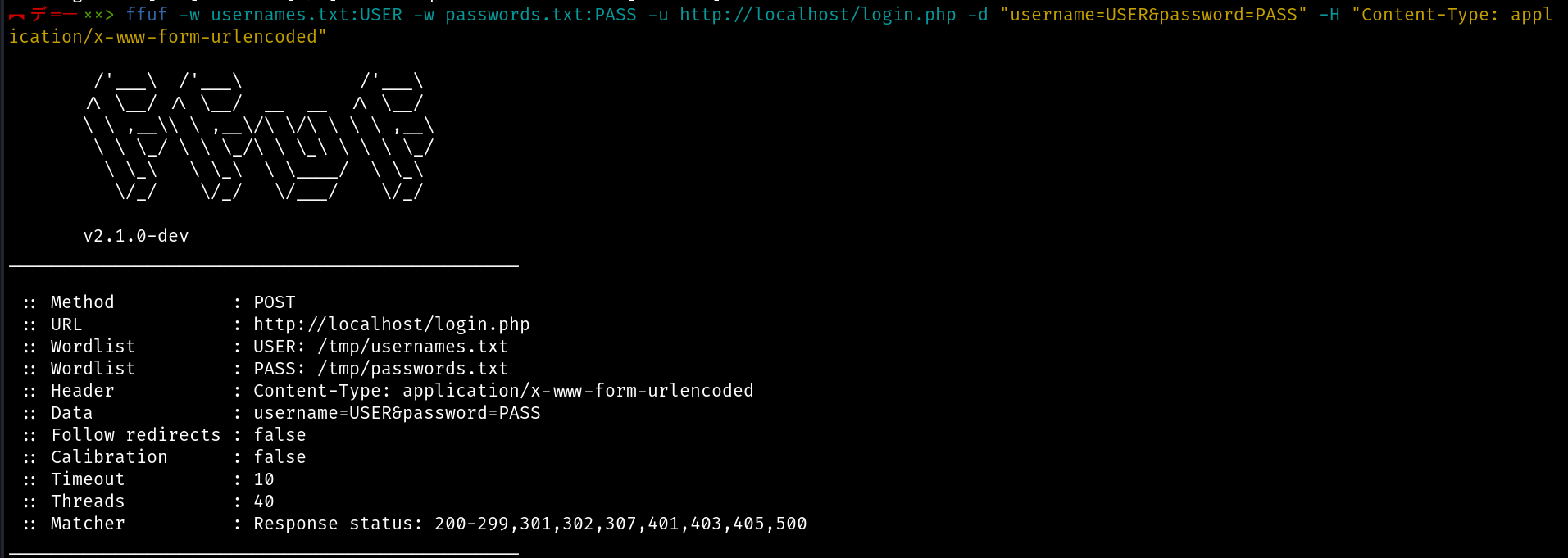
And as we can see, we were not able to brute force this even with valid credentials.
Even after trying various methods as shown above.
Brute Forcing Login page using BurpSuite
Lets try same with BurpSuite.
And the result is same as all of the tools. The server just can not understand what we are injecting.
Breaking The Curse of Encryption - Claiming The Control of Browser
Now we can understand how this Curse of Encryption affects the penetration testing. To overcome this challenge, a new approach is needed.
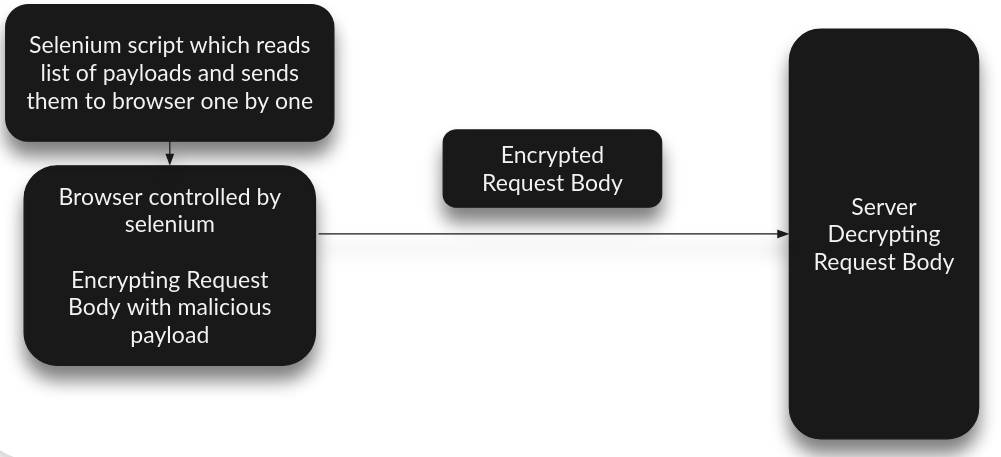
By automating the browser and testing web applications at the browser level, penetration testers can interact with web applications in the same way that a user would, bypassing the need to worry about encrypted traffic.
By automating the browser, testers can fill out forms, click buttons, and interact with dynamic elements on a web page, allowing them to identify vulnerabilities that may be hidden behind encryption. This approach not only improves the effectiveness of penetration testing but also saves time and effort compared to manual testing methods.
This innovative approach to web security testing laid the foundation for the development of The BrowserBruter, a tool designed to automate browser interactions and identify vulnerabilities in encrypted web applications.
Hence The BrowserBruter is born.
Finding SQL Injection using The BrowserBruter
Now using The BrowserBruter lets find the SQL Injection.
And we got time based SQL Injection!
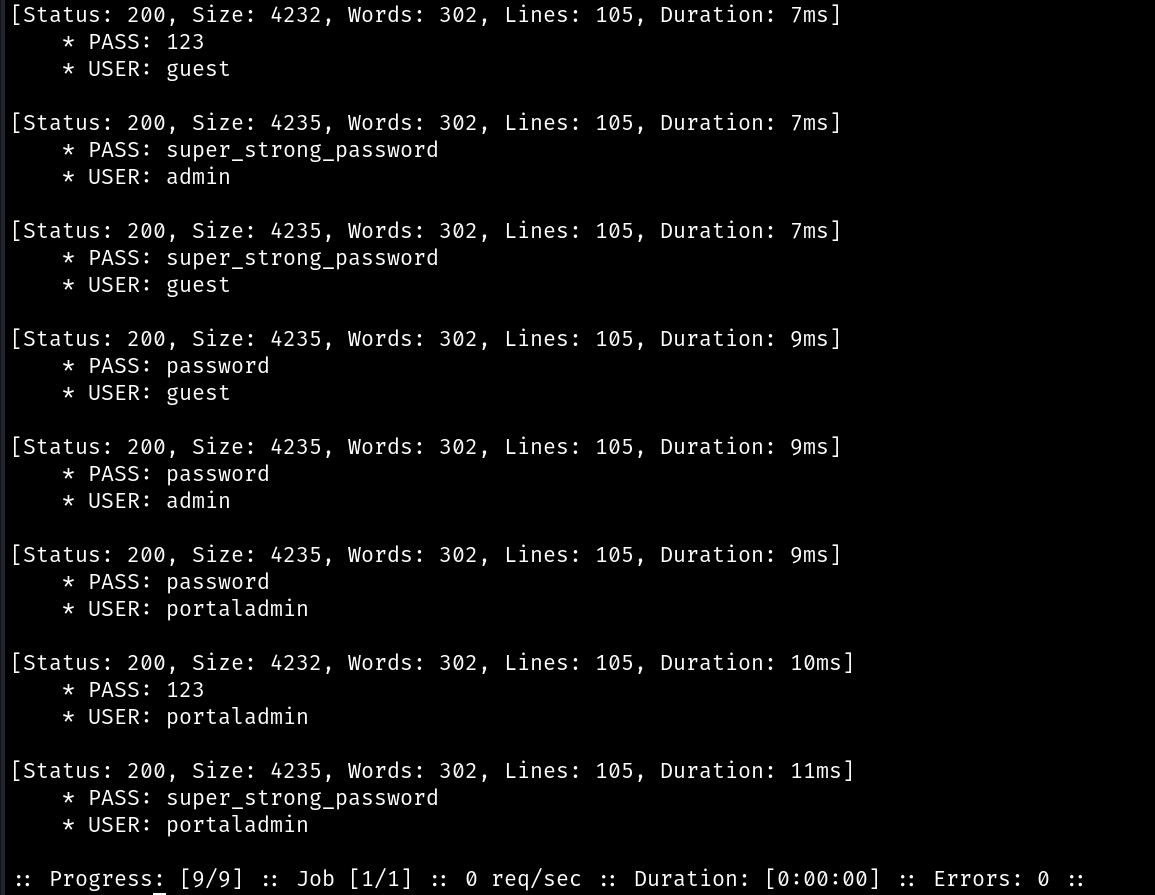
Successfully Brute Forcing Login page using The BrowserBruter
Now using The BrowserBruter lets brute force the login page to bypass the authentication.
And we got the valid credentials!
Limitation of Browser Bruter
Like every other tool, Browser Bruter has its limitations.
Slower Speed: Testing at the browser level inherently slows down the testing process compared to other automated testing methods. BrowserBruter's speed is limited by the browser's capabilities and the complexity of the web application being tested.
Complex Web Navigation: BrowserBruter can navigate complex web applications, but doing so can be challenging. The tool may struggle to accurately replicate all possible user interactions, especially in highly dynamic or intricate web environments.
Limited Web UI Interaction Coverage: While BrowserBruter can interact with web user interfaces (UI) to a certain extent, it may not cover all possible interactions. This limitation could result in missed vulnerabilities or incomplete testing coverage.
Please reach out to us for suggestion and help us improve this tool.
Hope on to the next section to learn about how to install & setup Browser Bruter test lab.