The Attack Modes
There are four attack modes in which The BrowserBruter can run. They are
- SNIPER
- BATTERING RAM
- PITCHFORK
- CLUSTER BOMB
Learn more about them here
The --attack switch can be used to select attack mode. The value for the --attack option can be either 1, 2, 3 or 4 with each representing respective attack modes as follows -
1 = SNIPER
2 = BATTERING RAM
3 = PITCHFORK
4 = CLUSTER BOMB
1. Sniper Attack
- The Sniper attack will take a single payload file.
- It will take a list of elements to fuzz.
- It will place single payload in single element until each element has fuzzed with that single payload. This will be repeated for each payloads.
- This attack mode is suitable for general penetration testing projects when you want to quickly find vulnerabilities and check the web application against bunch of payloads.
The --elements & --payloads option
The following options are required in this attack mode to specify elements and payloads -
--elements
--payloads
Here the --elements payloads is used to specify the comma separated list of elements to fuzz. For example, here we are specifying username and password elements to fuzz -
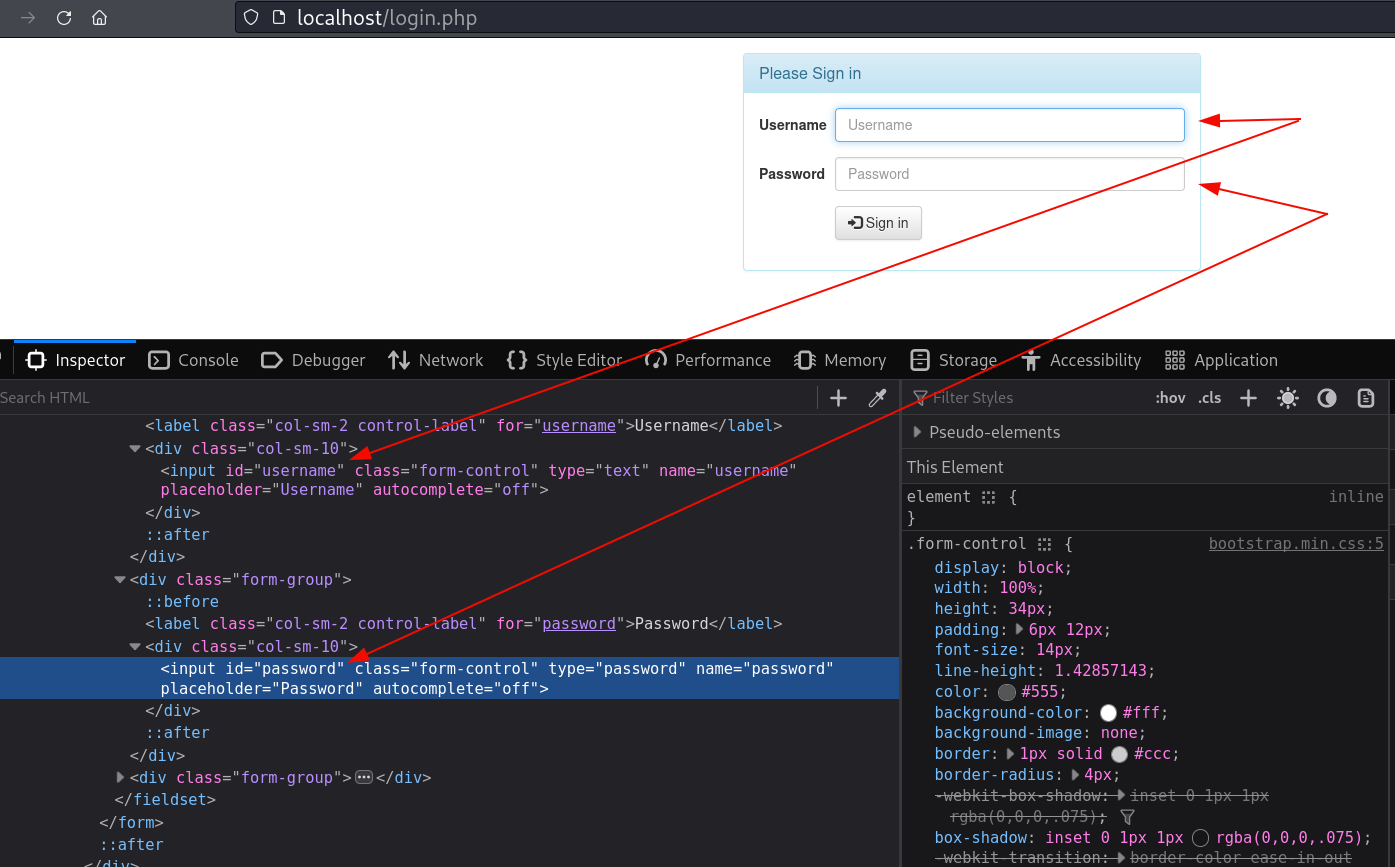
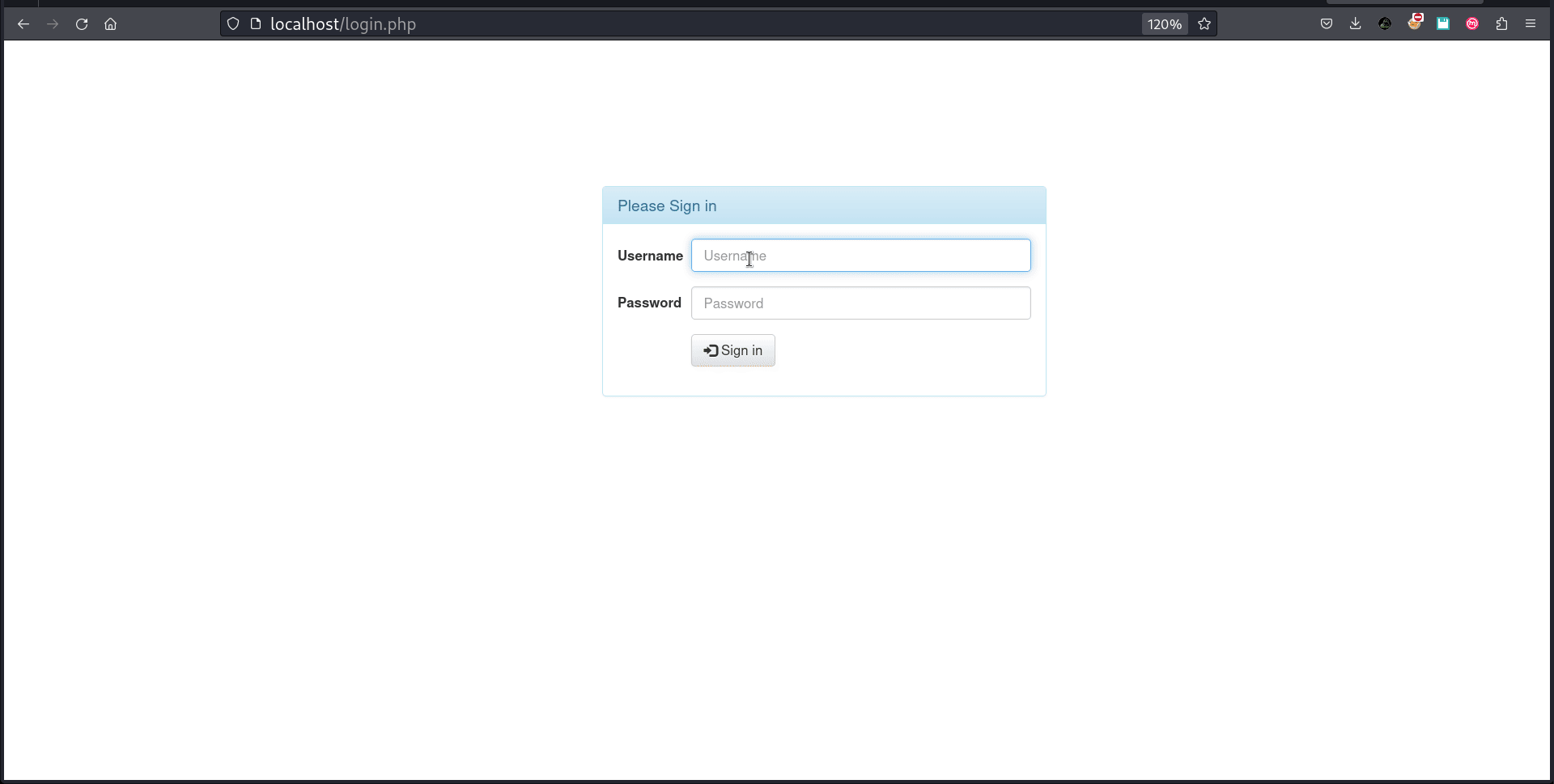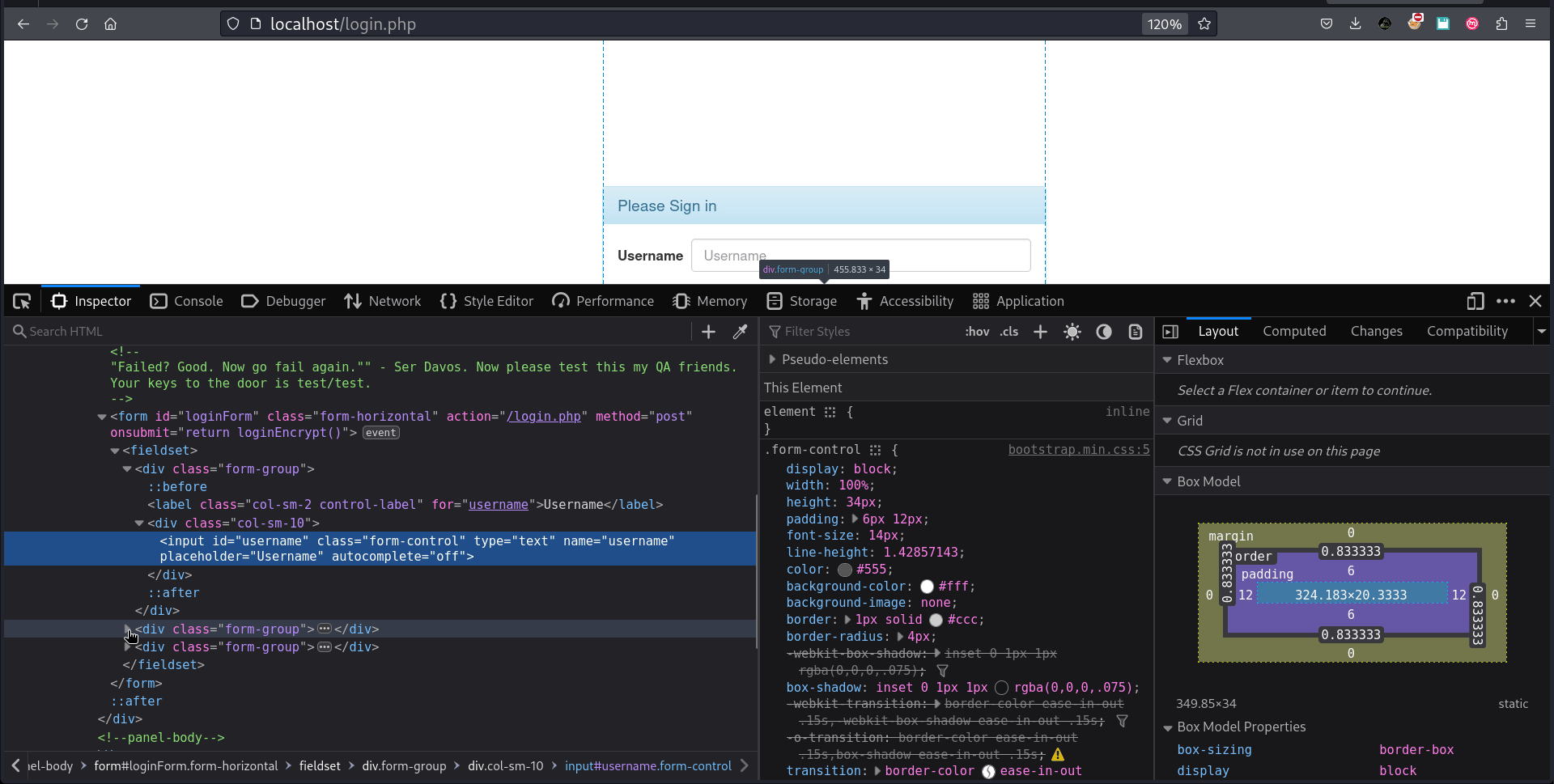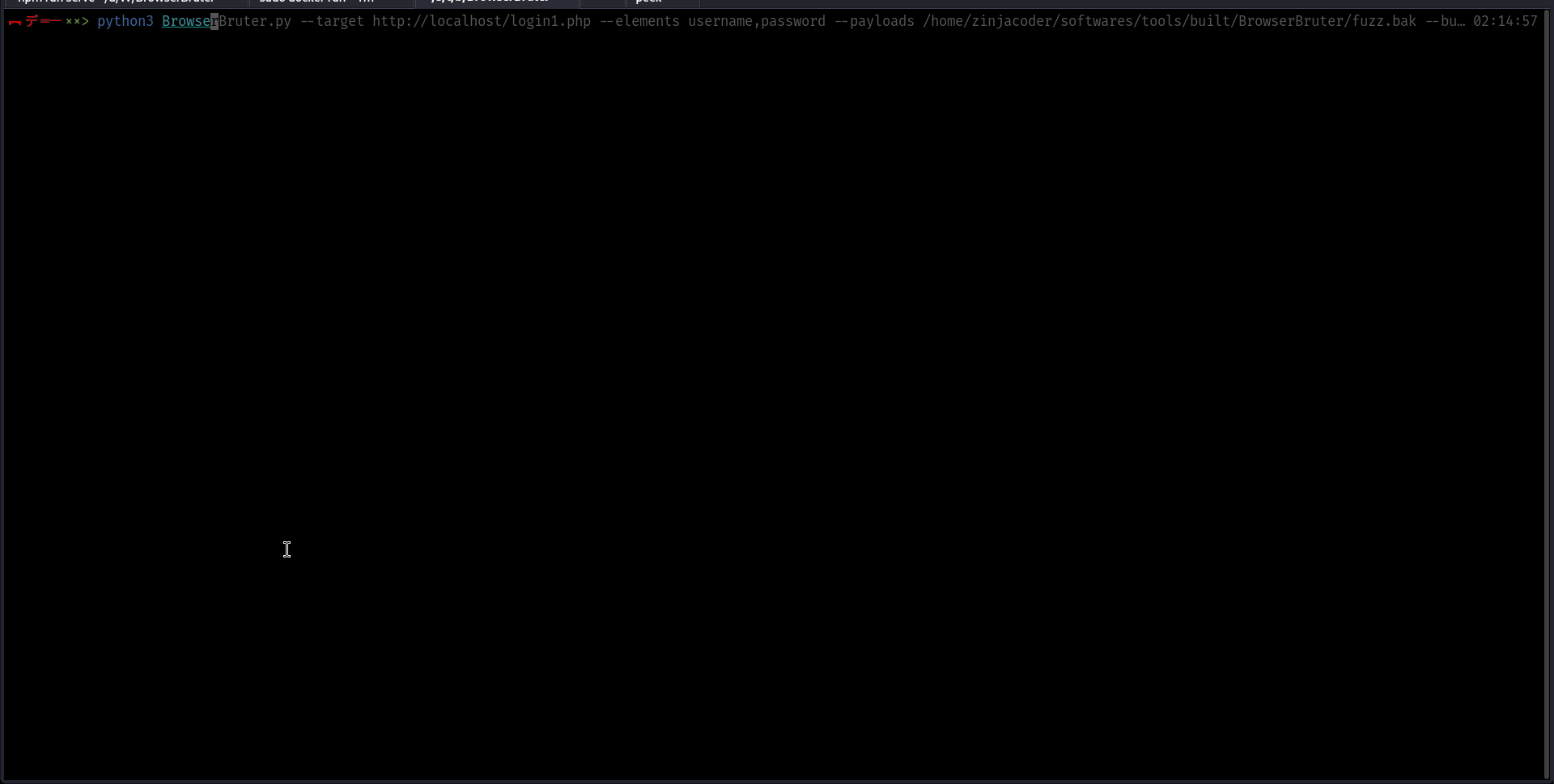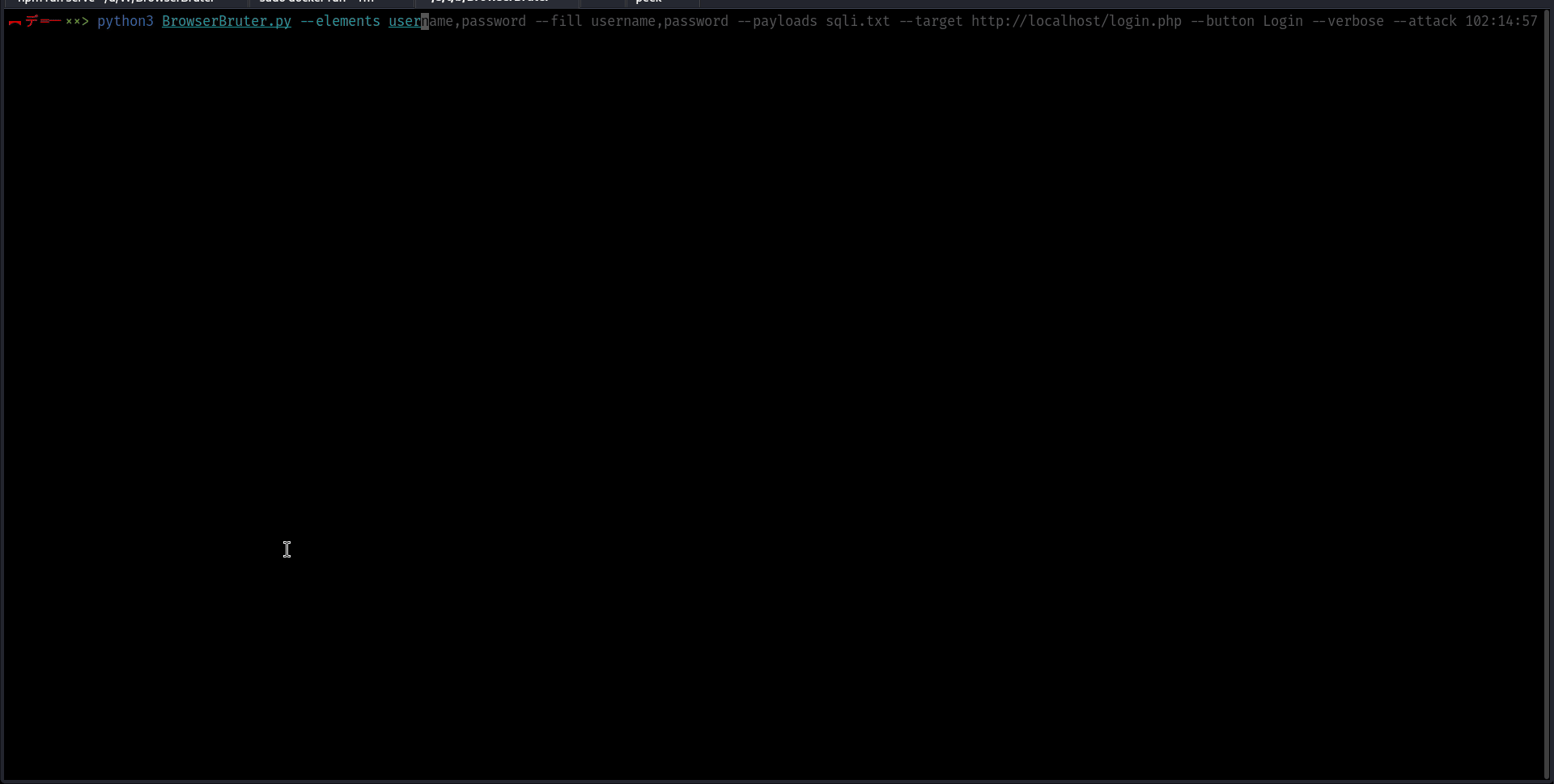
python3 BrowserBruter.py --elements username,password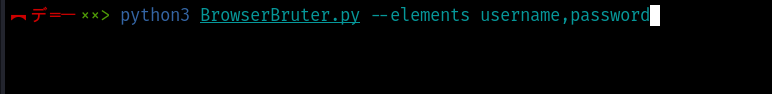
After specifying the elements to fuzz, we now have to specify the payloads file using --payloads option as shown below.
python3 BrowserBruter.py --elements username,passwords --payloads fuzz.txt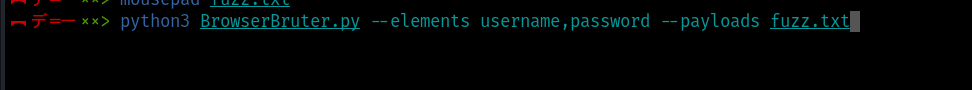
Now we need to specify the --target and --button options where --target is the URL of the page containing elements to fuzz and --button is the button element which trigger submission of the form.
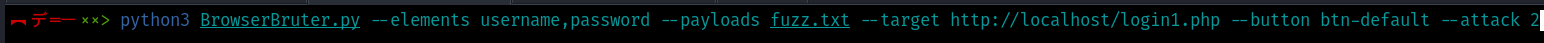
python3 BrowserBruter.py --elements username,passwords --payloads fuzz.txt --target http://localhost/login1.php --button btn-default
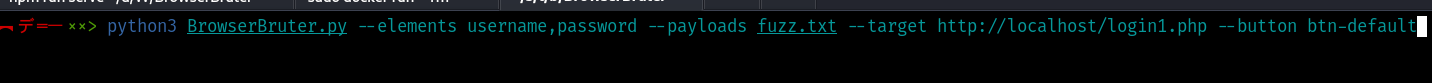
After that specify the attack mode as SNIPER using --attack 1 option.
python3 BrowserBruter.py --elements username,passwords --payloads fuzz.txt --target http://localhost/login1.php --button btn-default --attack 1
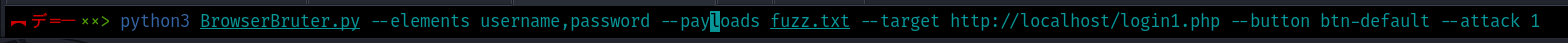
Then hit enter and unleash The BrowserBruter!
Here's what is happening:
- The BrowserBruter reads the and stores the payloads, let's assume there are three payloads in our list - [payload1, payload2, payload3]
- It then reads and prepares list of elements to be fuzzed which are - [username, password]
- It then navigates to the target URL.
- It then tries to find the 'username' and fills first payload from the payload's list which is 'payload1'.
- It then tries to find the '--button' element and clicks it.
- Then it again navigates to the target URL and finds 'password' field and inserts first payload from payload's list 'payload1' and submits it using '--button' element.
- It repeats this process until all payloads present in payload's list are filled and submitted in each elements to be fuzzed.
- This is how Sniper attack will work.
The --fill option
One thing that you will notice is that using above command might sometimes throw an error on web page like username field can not be blank or password field in required, for such cases specify the elements which are required to be filled in order to submit the form. The BrowserBruter will automatically fill the specified elements. More information on this option can be found here.
Re-run the above attack with --fill option to fill the required fields which are username and password.
python3 BrowserBruter.py --elements username,password --payloads fuzz.txt --target http://localhost/login1.php --button btn-default --attack 1 --fill username,password
Here's what is happening:
- The BrowserBruter reads the and stores the payloads, let's assume there are three payloads in our list - [payload1, payload2, payload3]
- It then reads and prepares list of elements to be fuzzed which are - [username, password]
- It then navigates to the target URL.
- It then tries to automatically fill the username and password field.
- It then tries to find the 'username' and fills first payload from the payload's list which is 'payload1'.
- It then tries to find the '--button' element and clicks it.
- Then it again navigates to the target URL and finds 'password' field and inserts first payload from payload's list 'payload1' and submits it using '--button' element.
- It repeats this process until all payloads present in payload's list are filled and submitted in each elements to be fuzzed.
- This is how Sniper attack will work.
No longer any errors related to empty fields after using --fill option.
2. Battering Ram Attack
The Battering Ram attack is same as Sniper attack with only difference is that it fills payloads in all input fields together instead of one by one like sniper attack.
If we continue our previous attack with Battering Ram -
python3 BrowserBruter.py --elements username,password --payloads fuzz.txt --target http://localhost/login1.php --button btn-default --attack 2
Here's what is happening:
- The BrowserBruter reads the and stores the payloads, let's assume there are three payloads in our list - [payload1, payload2, payload3]
- It then reads and prepares list of elements to be fuzzed which are - [username, password]
- It then navigates to the target URL.
- It then tries to find the 'username' and 'password` fills first payload from the payload's list which is 'payload1' in both of them (username,password) together.
- It then tries to find the '--button' element and clicks it.
- Then it again navigates to the target URL and finds 'password' field and inserts first payload from payload's list 'payload1' and submits it using '--button' element.
- It repeats this process until all payloads present in payload's list are filled and submitted.
- This is how Battering Ram attack will work.
Notice that here we are not using --fill option there are only two input fields in form and we are fuzzing them both, so in battering ram they both will be filled. If there were any third field which are not fuzzing then we can fill only that specific field using --fill option.
3. PitchFork Attack
The PitchFork and ClusterBomb does not requires --payloads or --elements options, instead they take combination of two --elements-payloads option.
The --elements-payloads option
The --elements-payloads option take values in following format element1:/path/to/payload-file-for-elements1.txt,element2:/path/to/payload-file-for-element2.txt,elementN:/path/to/payload-file-for-elementN.txt where element is the input field to be fuzzed and /path/to/payload-file is file containing payloads for that file.
Following is the working flow of PitchFork Attack:
- Get the list of elements and payloads from user.
- Create separate list of payloads for their respective elements.
- Start the Browser.
- Navigate to the target URL.
- Fill the payloads in their respective elements.
- Submit the form.
Here is an example which we are continuing from previous attacks for better understanding.
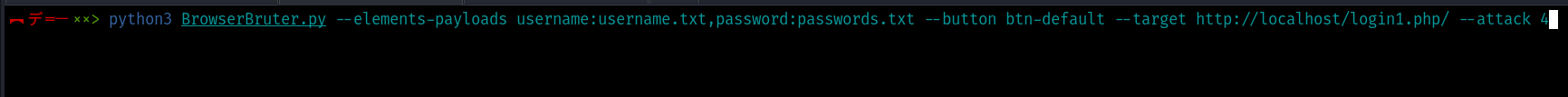
python3 BrowserBruter.py --elements-payloads username:usernames.txt,password:passwords.txt --target http://localhost/login1.php --button btn-default --attack 3
Here's what is happening:
Here in usernames.txt file I have following payloads-
admin
zin
hfs
In passwords.txt file I have following payloads-
pass
letmein
12345
- The BrowserBruter reads the and stores the payloads for their respective elements. So we have username->admin,zin,hfs & password->pass,letmein,12345.
- It then navigates to the target URL.
- It then tries to find the 'username' and 'password` fills first payload from the username payload's list which is 'admin' and fills first payload from password payload's list which is pass.
- It then tries to find the '--button' element and clicks it.
- Then it again navigates to the target URL and finds 'username' and 'password' fields and inserts second payloads from their respective payload's list 'zin' and 'letmein' and submits it using '--button' element.
- It repeats this process until all payloads present in each payload's list are filled and submitted.
- This is how PitchFork attack will work.
Note: The lists does not requires to have same amount of payloads. i.e. the usernames.txt and passwords.txt does not have to contain equal amount of payloads.
4. ClusterBomb Attack
The ClusterBomb same as PitchFork, does not requires --payloads or --elements options, instead they take combination of two --elements-payloads option.
The --elements-payloads option take values in following format element1:/path/to/payload-file-for-elements1.txt,element2:/path/to/payload-file-for-element2.txt,elementN:/path/to/payload-file-for-elementN.txt where element is the input field to be fuzzed and /path/to/payload-file is file containing payloads for that file.
Following is the working flow of ClusterBomb Attack:
- Get the list of elements and payloads from user.
- Create separate list of payloads for their respective elements.
- Prepare total possible combinations of payloads.
- Start the Browser.
- Navigate to the target URL.
- Fill the payloads in their respective elements.
- Submit the form.
- Repeat this for each possible combination of payloads.
Here is an example which we are continuing from previous attacks for better understanding.
python3 BrowserBruter.py --elements-payloads username:usernames.txt,password:passwords.txt --target http://localhost/login1.php --button btn-default --attack 4
Here's what is happening:
Here in usernames.txt file I have following payloads-
admin
zin
hfs
In passwords.txt file I have following payloads-
pass
letmein
12345
- The BrowserBruter reads the and stores the payloads for their respective elements. So we have username->admin,zin,hfs & password->pass,letmein,12345.
- It then prepares each possible combination of payloads as follows
admin:pass admin:letmein admin:12345 zin:pass zin:letmein zin:12345 hfs:pass hfs:letmein hfs:12345 - It then navigates to the target URL.
- It then tries to find the 'username' and 'password` fields and fills first payload combination of the payloads which is 'admin' and 'pass', then fills 'admin' in 'username' field and 'pass' in 'password' field.
- It then tries to find the '--button' element and clicks it.
- Then it again navigates to the target URL and finds 'username' and 'password' fields and inserts second payloads combination 'admin' in 'username' and 'letmein' in 'password' field and submits it using '--button' element.
- It repeats this process for all combinations of payloads.
- This is how ClusterBomb attack will work.
- It is useful in BruterForcing Authentication pages.
Note: The lists does not requires to have same amount of payloads. i.e. the usernames.txt and passwords.txt does not have to contain equal amount of payloads.
Note: The correct combination of username and password in authentication will result in successful authentication and will disrupt the remaining fuzzing process. To avoid this use --remove-session switch. Learn more.
The Result of the attack
Now we have finished our general attacks. Move on to the next section to learn about the result of the attack.